Block's Bitkey "Hardware Wallet" will Violate your Privacy and Security

Last month, the crypto industry erupted in scandal at the botched announcement of Ledger Recover. For some reason, Ledger thinks it is a good idea for crypto users to provide their KYC documents, split their seed between three custodians, and blindly trust Ledger's closed source hardware and software.
While Ledger fumbled the announcement (it was mistakenly referenced in the release notes of a firmware update), I was pleased to see so many prominent industry figures dissect the technical architecture, detail its flaws, and put immense pressure on Ledger to provide more information and delay or cancel their planned service.
My colleague, Seth for Privacy, wrote an excellent Twitter thread breaking down the severe issues with Ledger Recover.
Ledger is no stranger to scandal – its summer 2020 customer database leak damaged its reputation, and it has been under constant assault over its ultra-proprietary, closed source security architecture.
But I believe there is an upcoming product that, if widely adopted, is far more damaging to the crypto industry – that has the potential to violate the privacy and security of millions of future Bitcoiners. That product is Block's Bitkey.
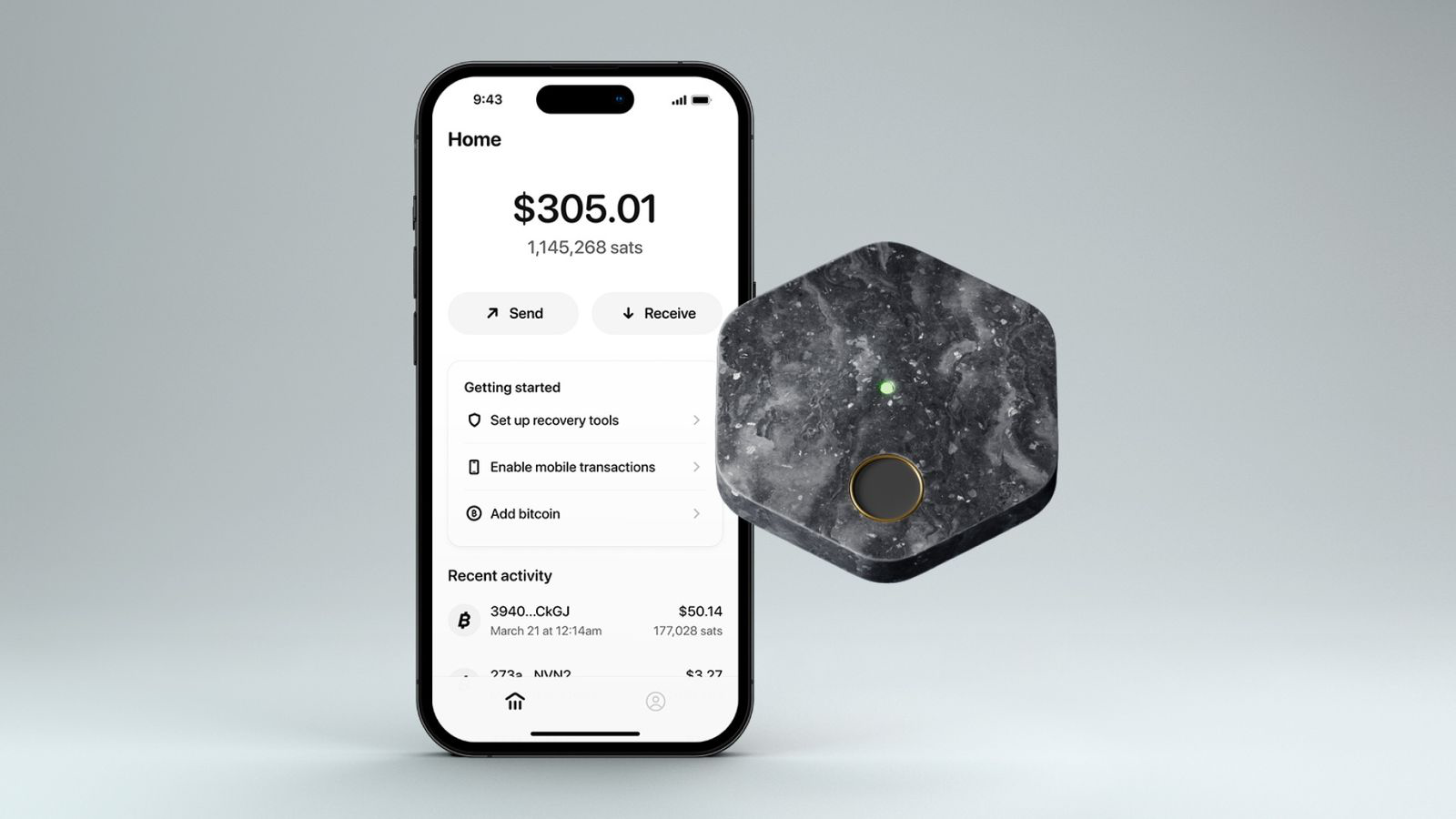
What is Bitkey?
Bitkey is commonly referred to as Jack Dorsey's upcoming Bitcoin hardware wallet. But the reality is more complex. Bitkey itself consists of three pieces:
- A mobile app that will allow users to store and purchase Bitcoin. At launch, Cash App and Coinbase will offer integrations.
- A hardware device, shaped like a hexagonal coaster, with integrated fingerprint reader and NFC connectivity. Note that Block never refers to this device as a "hardware wallet" – and neither will I.
- A server that can sign transactions and manage recovery scenarios.
Bitkey is, essentially, a 2-of-3 multisig service with one key on your phone, one key on a hardware device, and one key on the Bitkey server. At first, this does not sound too groundbreaking – Casa and Unchained, for example, have both operated similar services and allow users to connect third party hardware wallets.
But Bitkey departs from existing multisig offerings and hardware wallets in dangerous ways. I believe Bitkey is fundamentally flawed, provides terrible privacy and security, and should not come to market in its current form.
An Insecure Hardware Wallet
Compared to any mainstream hardware wallet, Bitkey offers woefully inadequate security.
Lack of Display
The original 2014 Ledger Nano did not have a display – it was just a USB smart card with a companion app. Very quickly Ledger realized that hardware wallets must allow users to confirm the full transaction details on a trusted display. This way, if the software wallet is compromised, the hardware wallet can catch any malicious behavior.

For example – let's say you are sending a Bitcoin transaction from your hardware wallet. If the address displayed on the hardware wallet's display does not match the address displayed on your software wallet, or if the amount of Bitcoin you are sending does not match, you know to immediately stop and assume your software wallet is compromised.
A hardware wallet's raison d'etre is to provide a trusted, offline environment for confirming transaction details before sending. Anything connected to the Internet has a greater likelihood of being compromised.
Of course, hardware wallets cannot protect against all types of attacks. There are certain cases where a compromised computer or phone could change the receive address in real time.
A malicious Chrome extension, for example, could modify the deposit address displayed on an exchange’s website. Then, when you go to send Bitcoin to the exchange, everything looks correct on your hardware wallet – but your funds are stolen because the Bitcoin receive address never belonged to the exchange.
This is why we still have to be extremely careful when sending large amounts of Bitcoin, and try to always verify addresses from multiple devices when possible. If you are depositing to an exchange, always verify that the receive address is the same on your web browser and the exchange's mobile app.
But a hardware wallet – with its trusted display – is capable of preventing so many common attacks! It gives you the ability to securely transact without needing to blindly trust your phone or computer.
If it does not have a screen, it’s not a hardware wallet. It’s just a 2FA device. It does not matter if the signing takes place on the device. Your software wallet is in charge. Your software wallet sends the unsigned transaction to the hardware wallet. If your hardware wallet doesn’t have a screen, you are fully trusting your software wallet – which completely negates the purpose of a hardware wallet!
Bitkey's hardware device does not include a display. The team attempts to offer an explanation in their blog post Screens are not a Panacea. Let me share some of my favorite quotes:
In practice, using a screen today means squinting and pecking through prompt after prompt, comparing alphanumeric strings and other details between the screen on the hardware wallet and the screen on whatever device you're using with it.
Small screens are hard to use, and often accompanied by user input mechanisms that are hard to use, too. We want to make self-custody more accessible -- and enabling customers to use their familiar phone screen as much as possible is a key enabler.
Using a screen correctly in order to provide protection is hard – customers have to know to compare their hardware wallet screen to an independent source on outgoing transfers, and to share receive addresses through multiple channels.
This post suggests that the complexity of tiny screens doesn't outweigh the practical benefit, and is one of the factors that keeps a broader audience from adopting self-custody.
The Bitkey team betrays a fundamental misunderstanding of hardware wallet security architecture and general Bitcoin threat modeling. They argue illogically that since a display does not protect you from every possible attack, it's not needed at all!
This is so dangerous from a company as respected as Block, and a CEO as respected as Jack Dorsey. Block is essentially telling its users to place full trust in its Bitkey mobile app, running on an internet connected smartphone. No need to verify any transaction details on your hardware wallet. Just blindly trust the Bitkey mobile app and blind-sign all your transactions on Bitkey hardware.
Block does have some proposed solutions to add more trust, and this sadly involves leveraging their server. We will cover that shortly.
Inability to Verify Multisig Addresses
Bitkey is a 2-of-3 multisig service. Multisig offers better security in certain conditions; if one of your three keys is lost or compromised, your funds are still safe. To spend your Bitcoin, you must sign a transaction from two of the keys.
This means that if someone steals your Bitkey hardware, they cannot use it to spend your funds. They would also need to steal your phone and access the Bitkey app, or log into the Bitkey app on a new phone and authorize a recovery with the Bitkey server. (Of course they would need to spoof your fingerprint as well.)
However, to securely receive Bitcoin to your Bitkey wallet, it is of paramount importance to verify the Bitcoin address actually belongs to your multisig!
Consider the steps to receive Bitcoin – open the Bitkey app, tap "Receive," and scan the QR code or copy-paste the displayed Bitcoin address. If your Bitkey app is compromised, how can you trust that it is showing you the correct address?
You cannot! Which is why hardware wallets with trusted displays are even more important when using multisig. On our Passport hardware wallet, for example, simply scan the QR code of the Bitcoin address and Passport will tell you if it belongs to your multisig. It's impossible to do that with Bitkey.
The Bitkey team is putting uncomfortably large amounts of trust in its mobile app. The Bitkey hardware will be unable to check if the mobile app is compromised. I believe there is no real purpose to the Bitkey hardware – it is effectively a 2FA device that holds one of the three multisig keys. It offers few meaningful security improvements over a Yubikey.
To mitigate some of these issues, Bitkey plans to leverage its server to verify everything occurring on its mobile app. Unfortunately, as I will outline below, the privacy and centralization concerns are enormous.
The Bitkey Server: A Surveillance Nightmare
It is important to note that, as described on their website, use of the Bitkey server is required. Unlike existing hardware wallets, which can be used with the app of your choice, all Bitkey users must use the Bitkey mobile app, Bitkey hardware, and Bitkey server.
This is not necessarily a bad thing. If done correctly, with good privacy practices, a server can be beneficial. For example:
- Blockstream's Jade hardware wallet offers no physical security, but it leverages Blockstream's server to rate-limit PIN attempts and therefore act as a virtual secure element. They cleverly call this a "blind oracle" – but it's effectively just their server. Notably, Blockstream allows technical users to self host their own "blind oracle" if desired.
- Our Passport hardware wallet includes a security check during setup. At the factory, a supply chain key is programmed into a slot in the secure element. Passport users can scan a QR code and communicate directly with validate.foundationdevices.com, which checks that the device has not been tampered with during transit.
- Our Envoy app includes a feature called Magic Backups, which takes an encrypted backup of all metadata on the user's mobile wallet, encrypts it with the seed, and backs it up to Foundation's server. There is no login, no email, and no identifying data collected. The hash of the seed acts as a username.
- Samourai's Whirlpool service requires a coordinator server, which Samourai runs. However, users connect via Tor, and advanced users can also run their own nodes for better privacy. Samourai does not have user accounts and does not know the identities of its users.
- Casa offers a 2-of-3 multisig service, but savvy users can sign up under a fake name and pay with Bitcoin. If they use a VPN or Tor, Casa knows nothing about their identities. Casa's server acts as a signer only if the user initiates a recovery transaction and it keeps recovery keys offline. Casa collects the public keys and can theoretically know user balances and transaction information – but it is possible to use pseudonymously.
Bitkey could have architected its server to collect as little information about users as possible – but it did not. The team seems to have done the opposite! The Bitkey server knows everything about its users.
Watching Every Transaction
The Bitkey server is effectively at the center of every transaction. Because Bitkey hardware lacks a trusted display, the server instead needs to verify transaction details in an attempt to ensure the mobile app is not compromised. The server effectively covers for the lackluster hardware.
To see how the Bitkey team thinks about its server, below is a quote from its Screens are not a Panacea blog post (emphasis my own):
Bitkey hardware can cryptographically sign information, the customer’s phone can forward that signature to Bitkey servers, and Bitkey servers can verify the signature in order to guarantee that the information was not modified in transit by the customer's phone, even if their phone is compromised by malware.
The reverse is also true -- Bitkey servers can sign information that can be verified by Bitkey hardware, ensuring that a compromised phone didn't tamper with information sent from server to hardware.
With the ability to send data securely between hardware and server, we can potentially use the server to do something the hardware cannot: communicate detailed transaction information like destination address, fees, and amounts directly to users.
That is, after receiving information like transaction details and receive addresses from the hardware, the server could communicate it, along with guidance about how to safely verify it, to a customer via channels like email, a webpage, or even one to one of their Trusted Contacts in the Social Recovery feature.
Note the bolded text. The Bitkey team is saying that it will use the server to email transaction details for verification, which could possibly take you to a webpage. This once again betrays a fundamental misunderstanding of threat modeling.
Picture this scenario: you want to send money to a friend, but you have malware on your phone and you are unaware that your Bitkey app is compromised.
You paste in your friend's Bitcoin address, type in your amount, and press Send. The Bitkey server emails you this information so that you can validate it.
But then you open the email...on your already compromised phone! And the malware swaps the Bitcoin address displayed in the email validation.
In this example, the transaction validation conducted by the server is useless because your internet connected device – your smartphone – is already infected with malware. Emails or webpages will not protect you.
A hardware wallet with trusted display would have trivially stopped this attack.
Don't Transact with Bitkey Users
It seems that the Bitkey team has considered the above scenario. Their proposed solution is to offer links to a special Bitkey webpage, unique to you. When you want to receive Bitcoin, simply share the link with your friend so she can "securely" confirm her address.
This means that simply transacting with a Bitkey user could compromise your privacy! From the same blog post:
Customers who want the additional confidence of a hardware-verified receive address could share a link with their intended recipient, who could view the receive address on a Bitkey-hosted page and check that it is indeed the address they want to be paid to ahead of the money being sent. In addition to providing strong protection against mobile malware, we think this approach could also help facilitate sharing addresses safely.
I recommend never opening a link sent from a Bitkey user. If you do, Block will be able to see your IP address and link your Bitcoin transaction directly to your IP. This is a blockchain analysis wet dream.
Automatic Server Signing
In addition to covering for hardware shortcomings, the Bitkey server will automatically sign transactions below a certain threshold for added convenience – but this means it is privy to all transaction details!
From How the wallet we're building works:
You can always move money without interacting with our servers by using the mobile key stored in the mobile app on your phone and the key stored in your hardware device – but we don’t expect you to do this for every transaction as you might want some more flexibility while still maintaining a high level of security.
For smaller transactions, you only need your mobile key stored in your phone, and we will provide the second key in response to you when you move your money with your mobile app. This lets you keep your hardware device tucked away somewhere safe and reserved for larger-sized transactions - or for the recovery capabilities it holds, which we discuss in a few questions below. We don’t expect you to bring the hardware device with you for daily usage - in fact, it’s safer to keep your mobile phone separate from the hardware device on a regular basis as both of those things (the mobile app and the hardware device) are needed together to move larger amounts of money.
I've compiled a list of information the Bitkey server will know about you:
- Your email address and any other login information. I'm not sure how Bitkey will perform 2FA for recovery, but they mentioned phone number and email as options.
- Your IP address, which reveals your physical location. I have not read anything about an option to connect to the Bitkey server via Tor for better privacy.
- The IP addresses of your counterparties if you share the link to your Bitkey's webpage to verify your transaction details with the help of the server.
- Your wallet balance and all transaction history. The Bitkey server acts as a signer in your 2-of-3 multisig, and therefore stores the three public keys. The server will see your entire transaction history – including the total amount of Bitcoin stored on Bitkey, and all addresses and amounts that you send to or receive from.
- For Cash App users – your KYC info, including name, date of birth, and social security number. Since Bitkey is designed to connect to Cash App, and since both are run by the same company, it is trivial to link your KYC data to your Bitkey wallet. Hopefully this will just be limited to Cash App, and not other partners like Coinbase – but I am not aware of what data will be shared.
Values and Principles?
To reiterate, the Bitkey team did not have pursue a technical architecture that surveils its users. They chose to do so. I've had the opportunity over the last year to chat with a couple Bitkey team members, and I think I understand their motivations. I think the Bitkey team is well-intentioned and approaching the product from a traditional finance perspective, instead of a cypherpunk / sovereignty / freedom perspective.
I think this is an enormous mistake.
Block's Cash App users are already accustomed to sharing all their financial data. To participate in today's fiat system, you have to have bank accounts and you have to share your KYC data. To link Cash App to your bank account, to get a credit card, to use ACH, you have no other option. Neither does Block.
But Bitcoin is a new system! An opportunity to start fresh, a potential to separate money and state. And even if you don't ascribe to these cypherpunk views (though ironically Jack Dorsey does) – Bitcoin at least represents an opportunity to build a more decentralized system.
So why the hell would you put an omniscient server at the center of what is supposed to be a self-custody product?
It's about values. It's about principles.
Bad for Sovereign Bitcoin Adoption
This is why I believe Bitkey is bad for Bitcoin – it represents an attack on the very idea of a hardware wallet; it represents an enormous privacy violation that many Bitcoiners are cheering for, unaware of the fine details of Bitkey’s architecture.
I admire the Bitkey team's pledge to open source the hardware and companion software. Will it also open source the code running server-side, which is apparently crucial to every aspect of the Bitkey product? How will Block protect user data when it knows every intimate detail of your transaction history?
I think, in the pursuit of a noble mission – to make an inexpensive and user friendly hardware wallet – Block has completely lost the plot. BitKey is not a hardware wallet. It's just a 2FA device.
Most scary to me, if Block is successful and distributes a billion units of Bitkey hardware, they will obtain the detailed financial information of a billion people. I am worried that, since Bitkey will be so cheap to manufacture (I estimate a $20-30 cost basis), Block will choose to give Bitkey away for free and profit from Bitcoin exchange fees.
New Bitcoiners would love a free hardware wallet from a reputable company. Except they'll have no idea that Bitkey is a surveillance product and that the Bitkey hardware is not at all a "hardware wallet." Bitcoin will continue to financialize, and private usage of Bitcoin will remain on the fringes.
This is not a future I want, and I do not think this is a future that Jack Dorsey wants. I think Block needs to reevaluate before bringing this product to the masses.
Disclaimer: I based this piece on the current blog posts on Bitkey's website. It's possible that the final Bitkey product may differ from what is documented on the website. Furthermore, as cofounder and CEO of Foundation, I am heavily biased.